
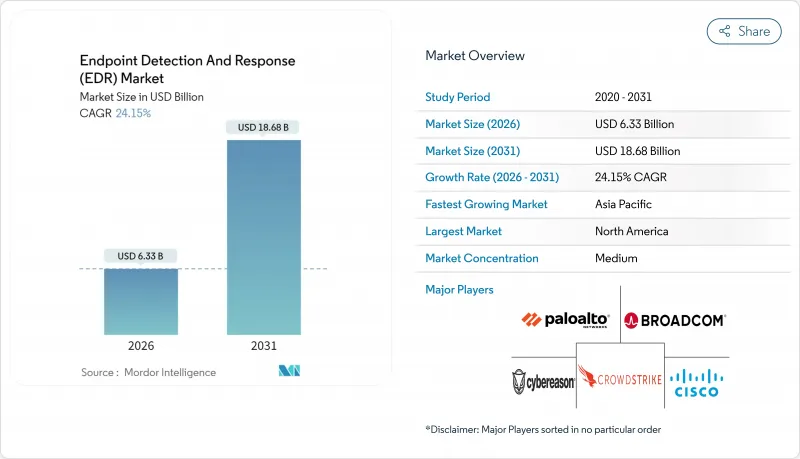
엔드포인트 탐지 및 대응(EDR) 시장 규모는 2026년에는 63억 3,000만 달러에 달할 것으로 예측됩니다.
이는 2025년 51억 달러에서 성장한 수치이며, 2031년에는 186억 8,000만 달러에 달할 것으로 전망되고 있습니다. 2026년부터 2031년까지 연평균 복합 성장률(CAGR)은 24.15%를 나타낼전망입니다.

성장을 이끌어내는 원동력은 2024년 9월까지 모든 민간기관에 EDR을 도입할 것을 의무화하는 미국 연방 정부의 구속력 있는 지침과 2025년 1월 이후 클라우드 워크로드와 ID 시스템으로 적용 범위를 확대하는 요건입니다. 또한 서비스형 랜섬웨어의 상용화, 제로 트러스트 보안 운영 센터로의 마이그레이션, 통합 에이전트 아키텍처에 대한 강한 수요가 플랫폼 구축을 가속화하고 있습니다. 소포스와 팔로알토 네트웍스의 인수가 상징하는 벤더 통합은 경쟁 환경을 재구성하고 있는 한편, 매니지드 서비스 채널은 비용에 민감한 중소기업 부문으로 전개를 확대하고 있습니다. 커널 레벨의 EDR 대책 툴킷이나 AI 구동형 경보의 수 폭증 등 기술적 과제가 이익률을 억제하고 있지만, 전체적인 성장세는 둔화되지 않았습니다.
대통령 행정명령 14028에 따라 300개가 넘는 미국 연방기관은 2024년 9월까지 풀스펙트럼 EDR의 도입이 의무화되었으며, 2025년 1월에는 적용 범위가 클라우드 워크로드와 ID 텔레메트리로 확대되었습니다. 방위산업기반의 계약자도 같은 요건을 반영해 2024년에는 EDR 예산을 4배로 확대하였습니다. 중요 인프라 사업자는 새로운 CISA 성능 목표를 준수하기 위해 FedRAMP 인증 솔루션을 채택했습니다. 주 및 지방 정부도 조성금 수급 자격 확보를 위해, 연방 기준과의 조화를 진행하고 있습니다. 따라서 정부 클라우드 인증을 받은 공급업체는 선호 후보 목록에 등재됩니다. 이 의무가 동맹국에도 파급됨에 따라 엔드포인트 탐지 및 대응(EDR) 시장은 컴플라이언스 주도의 지속적인 자극 효과를 얻고 있습니다.
LockBit 3.0 및 BlackCat과 같은 상용 랜섬웨어 키트는 사이버 범죄자의 진입 장벽을 낮추었고, 2024년에는 2,323건의 랜섬웨어 피해가 보고되었으며, 평균 금전 요구는 530만 달러로 상승했습니다. 의료 분야에서는 4,500만 건의 환자 기록이 유출되고 389건의 피해가 발생해 규제 당국은 HIPAA 보안 제도의 해석을 강화하고, 이로 인해 EDR 도입이 의무화되는 방향으로 흐르고 있습니다. 사업 중단 비용이 금전 지불액의 23배에 달하기 때문에 CFO는 EDR 투자를 업무 리스크 보험으로 파악하는 경향이 강해지고 있습니다. 이러한 경제적 변화는 모든 산업에서 엔드포인트 탐지 및 대응(EDR) 시장의 두 자릿수 성장을 지속하는 요인이 됩니다.
EDRKillShifter 및 Terminator와 같은 오픈소스 프레임워크는 커널 후크를 악용하여 엔드포인트 에이전트를 비활성화하거나 제거합니다. 이들은 연구실 평가에서 최대 90%의 회피 성공률을 달성했습니다. 500달러에 불과한 가격으로 공격자의 접근 범위가 넓어지고, 공급업체는 비용이 많이 드는 변조 방지 기술의 개발을 요구받으면서 출시 사이클이 장기화되고 있습니다. 또한 새로운 방어책이 이러한 툴킷을 무효화할 수 있다는 입증을 구매자가 기다리는 동안 일시적인 조달 지연이 발생합니다. 이로 인해 단기적인 확장이 억제되지만 엔드포인트 탐지 및 대응(EDR) 시장에서 장기적인 혁신이 강화됩니다.
엔드포인트 예방 플랫폼은 2025년 매출의 42.62%를 차지하였으며, 안티바이러스 방화벽 및 고도 탐지 기능을 통합한 단일 벤더 스위트에 대한 기업의 의존도를 부각하고 있습니다. 클라우드 워크로드 보호와 번들로 제공되는 클라우드 네이티브 EDR은 기존 에이전트에서 보호할 수 없는 마이크로서비스 배포와 서버리스 컴퓨팅의 혜택을 누리면서 26.20%의 연평균 복합 성장률(CAGR)로 가장 빠른 성장이 예상되는 하위 부문이 되었습니다. 신원 위협 탐지의 통합은 종합적인 노출 관리에 대한 시장의 발전을 시사합니다. 반면에 매니지드 EDR 및 MDR 채널은 중소기업에도 엔터프라이즈급 대응 범위를 제공합니다. 통합 에이전트에 연결되는 엔드포인트 탐지 및 대응(EDR) 시장 규모는 조직이 중복되는 포인트 솔루션을 폐지하고 통합 스택을 채택함에 따라 확대될 것으로 예측됩니다.
2차적인 영향은 신원, 클라우드 워크로드, 엔드포인트 텔레메트리 간의 융합을 가능하게 하는 데이터 공유 API를 둘러싼 경쟁 격화 및 이러한 데이터 플레인을 가로질러 동작하는 행동 분석에 대한 수요 증가를 포함합니다. 교차 도메인 가시성을 갖춘 경량 에이전트를 제공할 수 있는 공급업체는 업데이트 주기에서 우선 공급업체로서의 지위를 획득합니다. 반면에 단일 제품에 특화된 공급업체는 보다 광범위한 XDR 에코시스템과 통합하거나 합병하지 않는 한 상품화 위험에 직면합니다. 이 추세는 엔드포인트 탐지 및 대응(EDR) 시장에서 차별화 기준을 재구성하고 있습니다.
클라우드 제공 솔루션은 2025년에 엔드포인트 탐지 및 대응(EDR) 시장 규모의 66.48%를 차지하였으며, 원격 근무가 분산형 IT를 정상화하는 가운데 2031년까지 연평균 복합 성장률(CAGR) 25.90%로 확대를 계속할 전망입니다. 자동 업데이트, 중앙 집중식 정책, 확장 가능한 위협 인텔리전스 피드는 분산 워크포스에 강력한 이점을 제공합니다. 온프레미스 및 에어 갭 환경에서의 도입은 방위 분야 및 규제 대상 금융 업계에서 계속되고 있으며, 데이터 주권 요구 사항과 현대적인 탐지 기능을 양립하는 하이브리드 솔루션에 대한 수요를 견인하고 있습니다.
워크로드를 IaaS 플랫폼으로 마이그레이션하는 기업은 엔드포인트와 가상 머신 간에 동등한 보호를 요구하면서 SaaS형 탐지 솔루션 수요를 확대하고 있습니다. 종량 과금제는 자본 지출을 예측 가능한 운영 경비로 변환하며 이는 비용 관리 담당자에게 중요한 이점이 됩니다. 따라서 엔드포인트 탐지 및 대응(EDR) 시장은 클라우드 도입의 확대 곡선을 반영하고 있으며, 온프레미스 전용 노드는 규제로 인해 클라우드 처리가 명시적으로 금지되는 영역에서만 존재의의를 유지합니다.
북미는 대통령 행정명령 14028을 준수하고 첨단 민간 부문 위협 인텔리전스 공유를 통해 2025년 엔드포인트 탐지 및 대응(EDR) 시장의 37.02%를 차지했습니다. 2025년 1월 동 행정명령에 의해 클라우드 워크로드와 ID 시스템이 대상 범위에 추가되어 대응 가능한 엔드포인트 영역이 실질적으로 배증하면서 공급업체의 수익 전망을 개선했습니다. CISA의 자동 지표 공유 프로그램 등의 시책은 SOC 텔레메트리를 강화해, 분석 담당자의 과도한 부담 없이 검출 정밀도를 높이고 있습니다.
아시아태평양은 중국, 일본, 인도, 한국이 전국 규모의 사이버 보안 근대화 프로그램을 전개하는 가운데 2031년까지 26.10%의 연평균 복합 성장률(CAGR)을 나타낼 전망입니다. 클라우드 퍼스트 인프라 도입, 모바일 퍼스트 노동력, 국가 지원형 공격 활동의 격화로 조직은 SaaS형 EDR로 이행하고 있습니다. 중국의 '데이터 보안법'과 인도의 '디지털 개인정보 보호법' 등 국내 컴플라이언스 법령은 지속적인 엔드포인트 시각화를 의무화하고 있습니다. 지역 데이터센터와 현지 위협 조사 팀을 보유한 공급업체는 엔드포인트 탐지 및 대응(EDR) 시장의 이러한 고성장 영역에서 경쟁 우위를 확보하고 있습니다.
유럽에서는 2024년 10월에 18가지 중요한 분야에서 의무적인 사이버 대책의 적용 범위를 확대한 NIS2 지침을 발표함에 따라 꾸준한 확대가 예상됩니다. GDPR(EU 개인정보보호규정)의 위반 통지 및 과징금에 따라 EDR은 경영진의 우선 과제로서 더욱 중요성을 높이고 있습니다. 독일과 프랑스는 BSI와 ANSSI의 틀을 통해 도입을 주도하고 영국은 브렉시트 후 전략에서 주권 탄력과 다자간 협력을 중시하고 있습니다. 동유럽에서는 탐지 기술 업그레이드를 보조하는 EU 자금에 의해 도입이 가속하고 있습니다. 이러한 정책 주도의 동향은 거시경제적 압력에도 불구하고 엔드포인트 탐지 및 대응 업계에 건전한 수요를 유지하고 있습니다.
The endpoint detection and response market size in 2026 is estimated at USD 6.33 billion, growing from 2025 value of USD 5.1 billion with 2031 projections showing USD 18.68 billion, growing at 24.15% CAGR over 2026-2031.
Growth is propelled by binding U.S. federal mandates that require all civilian agencies to deploy EDR by September 2024 and, from January 2025, to extend coverage to cloud workloads and identity systems. Ransomware-as-a-service commercialization, the pivot to zero-trust security operations centers, and strong demand for unified-agent architectures further accelerate platform adoption. Vendor consolidation, highlighted by Sophos and Palo Alto Networks acquisitions, is reshaping competitive dynamics while managed service channels expand reach into the cost-sensitive SME segment. Technical headwinds such as kernel-level EDR-killer toolkits and AI-driven alert floods temper margins yet have not derailed overall momentum.
Executive Order 14028 forced more than 300 U.S. federal agencies to implement full-spectrum EDR by September 2024, then broadened the scope in January 2025 to include cloud workloads and identity telemetry. Contractors to the defense industrial base mirrored these requirements, quadrupling EDR budgets in 2024, while critical-infrastructure operators adopted FedRAMP-authorized solutions to align with new CISA performance goals. State and local governments are now harmonizing with federal benchmarks to secure grant eligibility. Vendors holding government cloud certifications, therefore, enjoy preferential shortlists. As mandates spill into allied nations, the endpoint detection and response market gains an enduring compliance-driven stimulus.
Commercialized ransomware kits such as LockBit 3.0 and BlackCat lowered the barrier to entry for cybercriminals, driving 2,323 reported ransomware events in 2024 and lifting average ransom demands to USD 5.3 million. Healthcare bore 389 of those incidents affecting 45 million patient records, causing regulators to tighten HIPAA security-rule interpretations that now favour mandatory EDR. CFOs increasingly view EDR spend as operational-risk insurance because business interruption costs reach 23 times the ransom payout. This economics shift sustains double-digit expansion of the endpoint detection and response market across all verticals.
Open-source frameworks like EDRKillShifter and Terminator exploit kernel hooks to blind or uninstall endpoint agents, achieving up to 90% bypass success in lab evaluations. Availability for as little as USD 500 widens attacker access, forcing vendors into costly tamper-proof engineering sprints and lengthening release cycles. Temporary procurement delays arise when buyers wait for proof that new defenses defeat these toolkits, trimming short-term expansion yet reinforcing long-term innovation in the endpoint detection and response market.
Other drivers and restraints analyzed in the detailed report include:
For complete list of drivers and restraints, kindly check the Table Of Contents.
Endpoint Prevention Platform accounted for 42.62% of 2025 revenue, underscoring enterprise reliance on single-vendor suites that unify antivirus, firewall, and advanced detection. Cloud-native EDR bundled with cloud workload protection is the fastest-growing subsegment at 26.20% CAGR, benefiting from microservice adoption and serverless compute that traditional agents cannot secure. Identity threat detection integration signals the market's evolution toward holistic exposure management, while managed EDR and MDR channels bring enterprise-grade coverage to smaller firms. The endpoint detection and response market size tied to unified agents is projected to multiply as organizations decommission overlapping point solutions in favour of a consolidated stack.
Second-order effects include heightened competition for data-sharing APIs that enable identity, cloud workload, and endpoint telemetry fusion, as well as rising demand for behavioural analytics that operate across these data planes. Vendors able to deliver lightweight agents with cross-domain visibility earn favoured-supplier status in renewal cycles. Conversely, point-product specialists risk commoditization unless they integrate or merge into broader XDR ecosystems. This dynamic is reshaping differentiation criteria inside the endpoint detection and response market.
Cloud-delivered solutions controlled 66.48% of the endpoint detection and response market size in 2025 and will continue expanding at a 25.90% CAGR to 2031 as remote work normalizes decentralized IT. Automatic updates, centralized policy, and elastic threat-intelligence feeds provide compelling advantages for distributed workforces. On-prem and air-gapped deployments persist in defense and regulated finance, driving hybrid offerings that reconcile data-sovereignty mandates with modern detection capabilities.
Enterprises shifting workloads to infrastructure-as-a-service platforms seek parity of protection across endpoints and virtual machines, amplifying demand for SaaS-delivered detection. Consumption-based pricing converts capital outlays into predictable operating expenses, a key benefit for cost controllers. The endpoint detection and response market, therefore, mirrors the broader cloud adoption curve, with specialized on-prem nodes retaining relevance only where regulation explicitly forbids cloud processing.
The Endpoint Detection and Response Market Report is Segmented by Solution Type (Endpoint Prevention Platform, Cloud-Native EDR/CWP-Integrated, and More), Deployment Model (Cloud-Delivered, On-prem/Air-gapped), End-User Vertical (BFSI, Healthcare, and More), Enterprise Size (Small and Medium Enterprises, Large Enterprises), and Geography. The Market Forecasts are Provided in Terms of Value (USD).
North America held a 37.02% endpoint detection and response market share in 2025 owing to Executive Order 14028 compliance and sophisticated private-sector threat intelligence sharing. The January 2025 order that added cloud workloads and identity systems effectively doubled the addressable endpoint universe, enhancing vendor revenue outlook. Programs such as CISA's Automated Indicator Sharing feed enrich SOC telemetry, sharpening detection without excessive analyst workload.
Asia-Pacific is projected to log a 26.10% CAGR through 2031 as China, Japan, India, and South Korea roll out nationwide cybersecurity modernization programs. Cloud-first infrastructure deployments, mobile-first workforces, and escalating state-sponsored attack activity pivot organizations toward SaaS-delivered EDR. Domestic compliance statutes such as China's Data Security Law and India's Digital Personal Data Protection Act compel continuous endpoint visibility. Vendors with regional data centers and local threat hunting teams gain competitive traction in this high-growth quadrant of the endpoint detection and response market.
Europe delivers steady expansion under the NIS2 Directive, which broadened mandatory cyber controls across 18 critical sectors in October 2024. GDPR's breach-notification fines further elevate EDR to boardroom priority. Germany and France spearhead adoption via BSI and ANSSI frameworks, while the U.K.'s post-Brexit strategy emphasizes sovereign resilience and multilateral partnerships. Eastern Europe accelerates through EU funding tranches that subsidize detection technology upgrades. These policy-driven dynamics maintain a healthy pipeline for the endpoint detection and response industry despite macroeconomic pressures.