
랜섬웨어 보호 시장 규모는 2025년에 258억 6,000만 달러, 2030년에는 554억 2,000만 달러에 이를 것으로 예상되며, CAGR은 16.5%를 나타낼 전망입니다.

ransomware-as-a-service의 생태계 확대, 트리플 추출 위협의 상승, 운영 기술에 의한 공격 대상의 확대로 지출의 기세는 쇠퇴하지 않습니다. 기업은 현재 암호화가 성공하더라도 비즈니스 연속성을 유지할 수 있도록 통합 예방, 감지 및 신속한 복구에 중점을 두고 있습니다. 클라우드 워크로드 노출, 세계 정보 공개 방법 강화, 사이버 보험 임계치 인상으로 예산은 제로 트러스트 제어, 불변 백업 및 행동 분석으로 이동하고 있습니다. 최종 사용자는 엔드포인트, 아이덴티티, 클라우드, 백업 기능과 매니지드 감지 및 대응 서비스를 융합한 통합 플랫폼을 선호하기 때문에 벤더의 통합이 격화되고 있습니다.
제네레이티브 AI에 의한 음성 클로닝이 기존의 피싱을 설득력 있는 '비싱'으로 바꿔 2025년에는 자격증 누설률을 증가시킵니다. Microsoft의 Defender XDR의 Phishing Triage Agent가 의심스러운 메시지에 자동 라벨을 붙여 보안 팀은 정확도를 높이면서 대응 사이클을 단축할 수 있게 되었습니다. 금융기관에 따르면 최근 정보 유출의 56%는 패치가 적용되지 않은 VPN 결함으로 인해 비정상적인 세션 활동에 플래그를 지정하는 사용자 엔티티 행동 분석을 도입하도록 촉구하고 있습니다. 소셜 엔지니어링 대책에 대한 주목이 높아짐에 따라 이메일, 엔드포인트 및 ID의 지속적인 모니터링에 대한 수요가 증가하고 있습니다.
언더그라운드 포럼에서 판매되는 활성 악성코드 키트의 절반 이상이 랜섬웨어의 변종이며 RaaS 운영자는 대개 공갈 요금의 10%-40%를 징수합니다. 기술적 장벽이 낮기 때문에 계열사는 산업기업을 공격할 수 있어 OT에 초점을 맞춘 인시던트가 87% 급증했습니다. 기업은 신흥 제휴 그룹 및 침해 시험판 지표를 핀 포인트로 식별하는 위협 인텔리전스 피드에 가입하기 시작했으며, 무기화되기 전에 검색 규칙을 업데이트할 수 있습니다.
Windows 및 주요 브라우저 플랫폼에 통합된 보호 기능은 추가 비용 없이 기본적인 멀웨어 방지 기능을 제공합니다. 이러한 도구는 상품화된 랜섬웨어를 억제하는 것, 행동 분석, 기만, 자동 롤백을 제공하는 것은 거의 없습니다. 중소기업 소유자 중 일부는 자신의 피해를 잘못 잘못하고 유상 업그레이드를 늦추고 전문 벤더의 예상 수익을 감소시키는 사람도 있습니다. 따라서 시판되는 공급업체는 고급 대응 기능, 공급망 원격 측정, 보험 적격성 보고서 등을 강조하여 보험료율을 정당화하고 있습니다.
2024년에는 On-Premise 구현이 매출의 68.7%를 차지하며 규제가 엄격한 기업에서 컴플라이언스 및 데이터 주권에 대한 요구를 뒷받침했습니다. 하지만 클라우드 구독은 2030년까지 연평균 복합 성장률(CAGR) 18.1%를 나타낼 전망입니다. 클라우드 제공 서비스의 랜섬웨어 보호 시장 규모는 구매자가 탄력적인 분석과 간소화된 업데이트를 수락함에 따라 급증할 것으로 예측됩니다. 로컬 센서와 SaaS 기반 상관 엔진을 결합한 하이브리드 설계가 표준이 되었으며, 팀은 텔레메트리를 현장에서 유지하면서 오프프레미스의 스케일을 활용할 수 있게 되었습니다.
자동화된 스냅샷 오케스트레이션은 평균 복구 시간을 단축합니다. Commvault의 Cloud Rewind는 전체 테넌트 환경을 몇 분 안에 복원할 수 있게 되었으며, 이전에는 복구 불확실성으로 인해 주저했던 조직의 관심을 끌고 있습니다. 지속적인 자세 모니터링, 통합 키 관리, 정책 애즈코드 파이프라인은 하드웨어 리프레시 사이클보다 DevSecOps의 무결성을 강조하는 개발 팀을 더욱 끌어들입니다.
엔드포인트 보호는 2024년 매출의 44.2%를 차지하며 랜섬웨어 방어 스택에서 최초로 구입하는 제품임에 변함이 없었습니다. 그럼에도 불구하고 백업 및 복구 CAGR은 17.2%로 용도 그룹에서 가장 높은 수치를 나타냅니다. 이뮤터블 에어 갭 리포지토리는 예방 레이어가 실패한 경우의 마지막 보증 역할을 합니다. ExaGrid의 네트워크를 향하지 않는 계층 및 지연 삭제 기능은 공격자가 복원 지점을 변조하는 것을 방지하는 설계의 예입니다.
전자 메일 및 웹 게이트웨이 모듈은 클라우드 검사 노드를 통해 트래픽을 라우팅하는 보안 액세스 서비스 에지 아키텍처를 통해 진화하여 분산된 워크포스 대기 시간을 줄입니다. 네트워크 세분화 기능도 이러한 플랫폼에 통합되어 봉쇄를 강화하는 동시에 카테고리 간의 경계를 모호하게 만듭니다. 구매자가 플랫폼 통합을 추진하는 가운데 벤더는 이전에는 엉망이었던 모듈을 통합 라이선스에 번들하여 랜섬웨어 보호 시장의 기세를 강화하는 패턴이 되고 있습니다.
랜섬웨어 보호 시장 보고서는 배포(On-Premise, 클라우드), 용도(엔드포인트 보호, 메일 보호 등), 최종 사용자 산업(은행, 금융서비스 및 보험(BFSI), 헬스케어 등), 조직 규모(대기업, 중소기업(SME)), 지역별로 분류됩니다.
북미는 2024년 매출액 점유율로 36.5%를 차지하며 금융과 헬스케어에 있어서 성숙한 컴플라이언스 체제와 기업예산의 규모가 큰 요인이 되었습니다. 중요 인프라에 대한 인시던트 보고 의무화와 같은 연방 정부의 이니셔티브는 보안에 대한 기본적인 기대를 더욱 강화하고 있습니다. 미국을 거점으로 하는 조직의 랜섬웨어 보호 시장 규모는 보험인수회사가 보상조건을 엄격화함에 따라 상승을 계속하고 있습니다.
아시아태평양의 2030년까지의 가장 빠른 CAGR 17.4%를 나타내는 호주에서는 랜섬 페이먼트의 공개를 의무화하는 새로운 법률이 시행되어 동남아시아에서는 2024년에 13만 5,000건을 넘는 랜섬웨어의 사례가 기록되는 등 아시아태평양의 피해가 부각되었습니다. APAC의 많은 정부는 중견 기업이 제로 트러스트 관리를 채택하도록 지원하는 보조금 프로그램을 시작하여 다국적 기업의 본사 이외에의 도입을 가속화하고 있습니다.
유럽에서는 NIS2 지령의 혜택으로 최대 15만 개의 중요한 기업이 대상이 되며 위반 시 벌금은 1,000만 유로로 설정됩니다. EU에 본사를 둔 중소기업은 위험 평가와 공급망 모니터링의 의무화를 실시하기 때문에 랜섬웨어 보호 시장 점유율이 상승할 것으로 예측됩니다. 반면 중동 및 아프리카에서는 기업이 2025년 보안 지출이 30억 달러 이상에 달할 것으로 예상됩니다. 라틴아메리카에서는 랜섬웨어 감염률이 세계 평균을 크게 상회하고 있으며, 브라질에서는 3일 이내의 정보 공개를 의무화하는 새로운 규제가 도입되는 등 관리형 보안 제공업체에게 지역적인 비즈니스 기회가 확대되고 있습니다.
The ransomware protection market size stands at USD 25.86 billion in 2025 and is forecast to climb to USD 55.42 billion by 2030, advancing at a 16.5% CAGR.
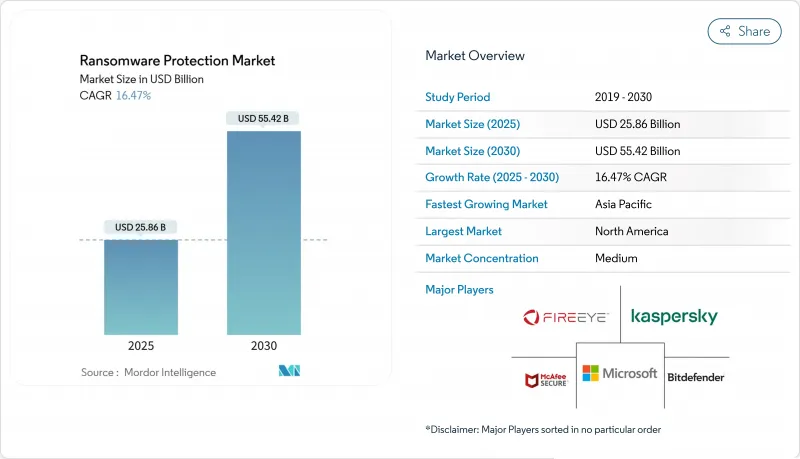
Expanding ransomware-as-a-service ecosystems, the rise of triple-extortion threats, and a widening operational-technology attack surface keep spending momentum strong. Enterprises now emphasize integrated prevention, detection, and rapid recovery so they can maintain business continuity even when encryption succeeds. Cloud workload exposure, tightening global disclosure laws, and higher cyber-insurance thresholds are shifting budgets toward zero-trust controls, immutable backups, and behavioral analytics. Vendor consolidation intensifies because end users favor unified platforms that blend endpoint, identity, cloud, and backup capabilities with managed detection and response services.
Generative-AI voice cloning turns conventional phishing into persuasive "vishing," increasing credential compromise rates in 2025. Microsoft's Phishing Triage Agent in Defender XDR now auto-labels suspicious messages, allowing security teams to shorten response cycles while boosting accuracy. Financial institutions say 56% of recent breaches originated from unpatched VPN flaws, pushing them to deploy user-entity behavior analytics that flag anomalous session activity. Heightened focus on social-engineering countermeasures fuels demand for continuous email, endpoint, and identity monitoring that work in concert rather than in silos.
More than half of active malware kits sold on underground forums are ransomware variants, and RaaS operators typically collect a 10%-40% cut of every extortion payment. Low technical barriers enable affiliates to attack industrial firms, driving an 87% surge in OT-focused incidents. Enterprises increasingly subscribe to threat-intelligence feeds that pinpoint emerging affiliate groups and pre-release indicators of compromise, allowing them to update detection rules before weaponization.
Integrated protections inside Windows and major browser platforms deliver baseline anti-malware at no added cost. While these tools curb commoditized ransomware strains, they rarely offer behavioral analytics, deception, or automated rollback. Some SMB owners, misjudging their exposure, delay paid upgrades, eroding prospective revenue for specialist vendors. Commercial suppliers therefore highlight advanced response functions, supply-chain telemetry, and insurance-eligibility reports to justify premium tiers.
Other drivers and restraints analyzed in the detailed report include:
For complete list of drivers and restraints, kindly check the Table Of Contents.
In 2024, on-premises implementations accounted for 68.7% of revenue, underlining compliance and data-sovereignty demands among heavily regulated enterprises. Nevertheless, cloud subscriptions are sprinting forward at an 18.1% CAGR through 2030. The ransomware protection market size for cloud-delivered offerings is projected to rise sharply as buyers embrace elastic analytics and simplified updates. Hybrid designs are now standard, pairing local sensors with SaaS-based correlation engines so teams keep telemetry on-site while leveraging off-premises scale.
Automated snapshot orchestration shortens mean time to recover. Commvault's Cloud Rewind now restores full tenant environments in minutes, rallying interest from organizations that previously hesitated due to recovery uncertainty. Continuous posture monitoring, integrated key management, and policy-as-code pipelines further attract development teams that favor DevSecOps alignment over hardware refresh cycles.
Endpoint protection delivered 44.2% of 2024 revenue and remains the first purchase in any ransomware defence stack. Still, backup and recovery are on track for a 17.2% CAGR, the highest among application groups. Immutable and air-gapped repositories now act as a last-line assurance when prevention layers fail. ExaGrid's non-network-facing tier and delayed delete feature exemplify designs that stop attackers from tampering with restore points.
Email and web-gateway modules evolve via secure access service edge architectures that route traffic through cloud inspection nodes, lowering latency for distributed workforces. Network segmentation features also move into these platforms, blurring lines between categories while strengthening containment. As buyers push toward platform consolidation, vendors bundle previously discrete modules into unified licences, a pattern reinforcing the ransomware protection market momentum.
The Ransomware Protection Market Report is Segmented by Deployment (On-Premises and Cloud), Application (Endpoint Protection, Email Protection, and More), End-User Industry (BFSI, Healthcare, and More), Organization Size (Large Enterprises and Small and Medium Enterprises (SMEs)), and Geography.
North America led with 36.5% revenue share in 2024, anchored by mature compliance regimes in finance and healthcare plus sizeable enterprise budgets. Federal initiatives such as mandatory incident reporting for critical infrastructure further elevate baseline security expectations. The ransomware protection market size for United States-based organizations will continue to climb as insurance underwriters harden coverage terms.
Asia-Pacific posts the fastest 17.4% CAGR to 2030. New laws in Australia require ransom-payment disclosures, and Southeast Asia recorded more than 135,000 ransomware cases in 2024, spotlighting regional exposure. Many APAC governments launch subsidy programs that help mid-market firms adopt zero-trust controls, accelerating uptake beyond multinational headquarters.
Europe benefits from the NIS2 directive, which covers up to 150,000 essential entities and sets fines at EUR 10 million for non-compliance. The ransomware protection market share for EU-based SMEs is expected to rise as they implement mandatory risk assessments and supply-chain monitoring. Meanwhile, the Middle East and Africa foresee security outlays exceeding USD 3 billion in 2025 as enterprises invest in generative-AI analytics and breach-response retainers. Latin America grapples with a ransomware involvement rate notably higher than the global average, driving new regulation in Brazil that forces disclosure within three days, thereby enlarging regional opportunity for managed security providers.