
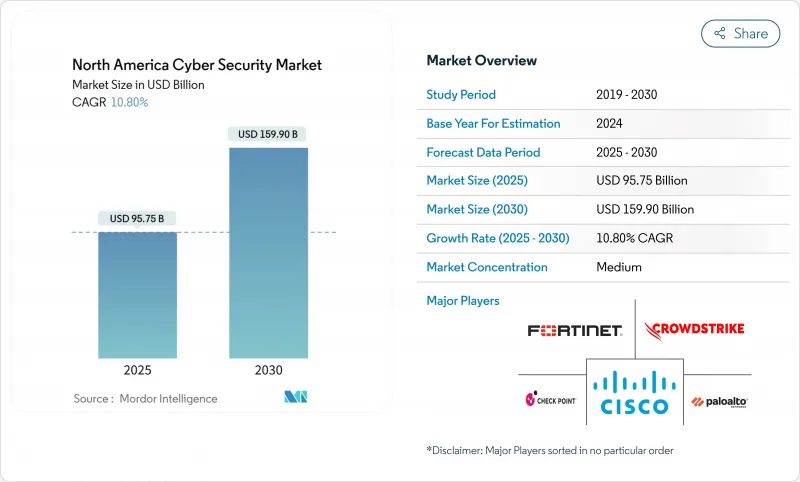
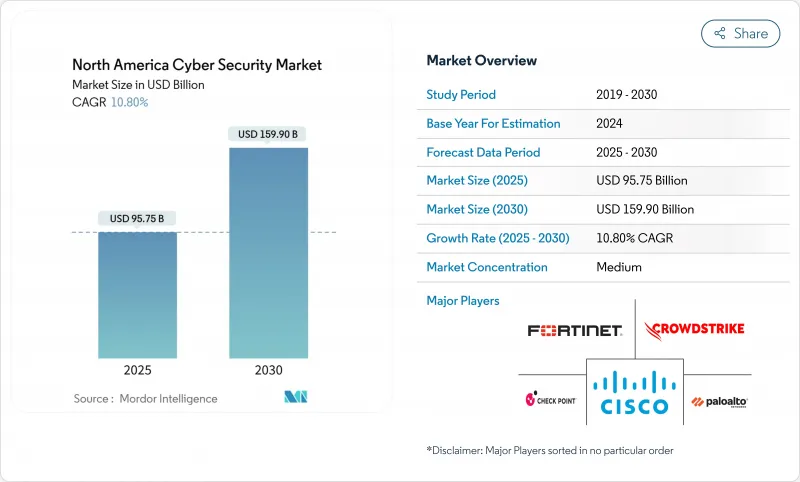
북미의 사이버 보안 시장 규모는 2025년에 957억 5,000만 달러로 추정되며, 예측 기간(2025-2030년)의 CAGR은 10.80%로, 2030년에는 1,599억 달러에 달할 것으로 예측됩니다.
엄격한 연방 및 주 규제, 첨단 위협의 확산, 중요한 산업에서 디지털 변혁 프로그램의 가속화가 주요 성장 엔진이되었습니다. 미국 50개 주 모두에서 위반정보공개가 의무화되어 증권거래위원회의 새로운 보고규칙이 완성됨에 따라 기업은 순수한 사후 대응형 인시던트 리스폰스 모델이 아니라 예방형 컨트롤에 대한 투자를 강요하고 있습니다. 게다가 2030-2035년까지 암호화 시스템의 오버홀을 정부 기관이나 계약자에게 의무화하는 연방 정부의 포스트 양자암호로의 전환이 지출에 박차를 가하고 있습니다. 미국은 지역별 수요의 대부분을 차지하고 있지만, 캐나다는 법안 C-26에 의해 중요한 시스템 요건이 강화되고, 벤더의 활동이 활발해지면서 가장 급속히 확대하고 있습니다. 기업이 기술 격차를 메우기 위해 보안 운영을 아웃소싱하기 때문에 관리 서비스와 전문 서비스의 성장이 가속화되고 있습니다.
미 증권거래위원회(SEC)는 태양광 윈즈 관련 정보 공개에 미비한 것으로 상장 기술 기업 4개사에 700만 달러의 벌금을 부과했습니다. 2024 회계연도 동안 583건의 강제조치와 82억 달러의 구제조치가 실시됨에 따라 이사회는 사이버 보안을 재량적인 IT 지출이 아니라 핵심 컴플라이언스 기능으로 취급하도록 요구되었습니다. 동시에 멕시코에서는 2024년도에 4,240만 건의 악성코드 시도가 기록되어 하루 11만 6,000건에 이르렀습니다. 미국에서는 각 주가 통지법령을 시행하고, 연방규칙에서는 중대 사건으로부터 4영업일 이내의 공개가 의무화되어 있기 때문에 기업은 지속적인 감시, 자동검출, 대응 사이클의 단축과 배상 책임의 상한을 설정하는 침해 봉쇄 플랫폼으로 예산을 이동하고 있습니다.
연방정부의 행정명령과 NIST SP 800-207이 공공 부문의 디폴트로서 아이덴티티 중시의 아키텍처를 확립했을 때 제로트러스트 모델은 경계 중심의 전략을 대체했습니다. 오늘날 북미 기업의 60%가 제로 트러스트 프로그램을 적극적으로 실시하고 있으며, 94%가 적어도 하나의 요소를 도입하고 있습니다. 이 마이그레이션은 네트워크 에지와 인증 흐름을 재구성하는 지속적인 클라우드 배포의 파도와 분리 할 수없는 관계에 있습니다. 하이브리드 또는 멀티클라우드 환경에서 제로 트러스트를 도입한 조직은 인시던트 처리 및 정책 유지보수 부담을 줄임으로써 152%의 ROI를 보고했습니다. 클라우드 마이그레이션과 제로 트러스트 툴의 합류는 보안 액세스 서비스 에지(SASE)와 아이덴티티 앤 액세스 관리 플랫폼에 대한 수요를 촉진하고 멀티클라우드 거버넌스를 전문으로 하는 MSSP의 구조적인 서비스 기회를 강화하고 있습니다.
북미에서는 2024년에 고용자 수가 2.7% 삭감된 후에도 사이버 보안 포지션이 4% 증가했고 54만 2,687개의 포지션이 2025년에 비어 있습니다. 예산 동결에 휩싸인 기업은 37%에 이르렀지만, 그래도 90%는 특히 AI를 활용한 애널리틱스와 제로 트러스트 구성에 있어서 중대한 스킬 갭을 보고하고 있습니다. 멕시코만으로도 2025년까지 3만 5,000명의 전문가가 필요하지만, 현지 기업의 65%가 인재 부족을 최대 장벽으로 꼽고 있으며, 이를 보완하기 위해 첨단 기술 지출이 80% 증가하고 있습니다. 기술 부족으로 인해 기업은 장기간의 체류에 노출되어 인력 부족 팀으로 인한 침해의 직접적인 손실은 평균 400만 달러에 이르러 기술과 전문 지식을 구독 패키지로 정리한 매니지드 검지·대응 서비스의 채용이 급선무가 되고 있습니다.
2024년 북미의 사이버 보안 시장의 65.5%는 솔루션이 차지했지만 2030년까지의 CAGR은 13.8%를 나타낼 전망입니다. 서비스 증가 추세는 기술 부족을 직접 완화하는 동시에 기업에 AI 주도 분석 플랫폼에 신속한 액세스를 제공합니다. 양자 안전 암호 평가 및 제로 트러스트 로드맵 작성을 위한 전문 서비스도 증가하고 있습니다. eSentire는 현재 250만 명의 환자 데이터를 보호하고 있으며 규제 분야 수요를 뒷받침하고 있습니다.
북미의 관리 서비스의 사이버 보안 시장 규모는 건강 관리와 중견 제조업 사이에서 가장 빠르게 확대되고 있습니다. 서비스 기반 소비 모델은 사이버 보안을 영업 비용으로 취급함으로써 기업이 엄청난 툴 세트를 통합하고 이사회 승인을 얻는 데 도움이 됩니다. 벤더는 AI, 위협 인텔리전스, 인간의 전문지식을 번들로써 점착성이 높은 다년 계약을 획득하여 경상수익의 가시성을 높입니다.
2024년 북미의 사이버 보안 시장 규모의 56.2%는 여전히 On-Premise가 차지했지만, 하이브리드 워크에 의해 경계 중심의 갭이 노출됨에 따라 클라우드 보안 지출은 CAGR 17.2%를 나타낼 전망입니다. 연방 정부에 의한 제로 트러스트 지령과 클라우드 퍼스트 전략에 관한 대통령령이 결합되어 방위·민간 기관에 있어서의 클라우드 네이티브의 채용이 가속하고 있습니다. 민간 기업은 자본 투자 감소, 정책 오케스트레이션 통합, 지속적인 컴플라이언스 실현 등의 이점이 있습니다.
대기업은 데이터 주권을 위해 하이브리드 모델을 운영하고 중소기업은 완전히 관리되는 클라우드 보안 서비스 에지로 이동합니다. Oracle의 제로 트러스트 클라우드 제어 프레임 워크는 신원 거버넌스, 마이크로 세분화 및 암호화가 어떻게 융합되고 공격 표면을 강화하는지 보여줍니다. 정책 작성 및 구성 오류 복구를 자동화하는 공급업체는 멀티클라우드의 복잡성이 확대됨에 따라 지지를 받고 있습니다.
북미의 사이버 보안 시장은 제공 형태(솔루션 및 서비스), 배포 형태(클라우드 및 On-Premise), 조직 규모(중소기업 및 대기업), 최종 사용자(은행, 금융서비스 및 보험(BFSI), 헬스케어, IT 및 텔레콤 등), 국가별로 구분됩니다. 시장 예측은 금액(달러)으로 제공됩니다.
The North America Cyber Security Market size is estimated at USD 95.75 billion in 2025, and is expected to reach USD 159.90 billion by 2030, at a CAGR of 10.80% during the forecast period (2025-2030).
Stringent federal and state regulations, the spread of sophisticated threats, and accelerated digital-transformation programs across critical industries are the primary growth engines. Mandatory breach-disclosure laws in all 50 U.S. states and new Securities and Exchange Commission reporting rules compel firms to invest in preventive controls instead of purely reactive incident response models. Spending is further fueled by the federal transition to post-quantum cryptography, which requires agencies and contractors to overhaul encryption systems by 2030-2035. The United States retains the lion's share of regional demand, yet Canada registers the fastest expansion as Bill C-26 tightens critical-system requirements and stimulates vendor activity. Across offerings, solutions still represent 65.5% of revenue, although managed and professional services are growing faster as enterprises outsource security operations to close skills gaps.
Regulatory scrutiny intensified when the SEC levied USD 7 million in penalties on four listed technology companies for deficient SolarWinds-related disclosures, underscoring that incomplete cyber-risk reporting now carries tangible financial consequences. Coupled with 583 enforcement actions and USD 8.2 billion in remedies during fiscal 2024, the climate pushes boards to treat cybersecurity as a core compliance function rather than a discretionary IT spend. At the same time, Mexico logged 42.4 million malware attempts in 2024-116,000 per day-reflecting the wider regional surge in threat volume that now hits manufacturing hardest. Because every U.S. state enforces a notification statute and federal rules require disclosure within four business days of a material incident, enterprises have shifted budgets toward continuous monitoring, automated detection, and breach-containment platforms that shorten response cycles and cap liability.
Zero-trust models replaced perimeter-centric strategies once federal Executive Orders and NIST SP 800-207 established identity-focused architectures as the public-sector default. Today, 60% of North American enterprises have an active zero-trust program, and 94% have deployed at least one element; the transition is inseparable from sustained cloud-adoption waves that re-shape network edges and authentication flows. Organizations implementing zero-trust within hybrid or multi-cloud environments report 152% ROI through diminished incident handling and policy-maintenance burdens, a finding that resonates with finance and healthcare entities balancing regulatory mandates with cost discipline. The confluence of cloud migration and zero-trust tooling propels demand for secure access service edge (SASE) and identity-and-access-management platforms, reinforcing a structural service opportunity for MSSPs that specialize in multi-cloud governance.
North America entered 2025 with 542,687 open cybersecurity positions, a 4% increase even after employer headcount cuts of 2.7% in 2024. Budget freezes struck 37% of firms, but 90% still reported material skill gaps, particularly in AI-enabled analytics and zero-trust configuration. Mexico alone needs 35,000 specialists by 2025, yet 65% of local organizations cite talent scarcity as their top barrier, triggering an 80% uptick in advanced-technology spending to compensate. Skills shortages expose enterprises to prolonged dwell times, and breaches blamed on understaffed teams averaged USD 4 million in direct losses, adding pressure to adopt managed detection and response services that wrap technology and expertise in subscription packages.
Other drivers and restraints analyzed in the detailed report include:
For complete list of drivers and restraints, kindly check the Table Of Contents.
Solutions retained a 65.5% share of the North America cybersecurity market in 2024, yet services are on pace for 13.8% CAGR through 2030 as organizations outsource 24/7 monitoring to counter evolving threats. The services uptrend directly mitigates the skills shortage while giving firms rapid access to AI-driven analytics platforms. Professional services for quantum-safe cryptography assessments and zero-trust road-mapping have also risen. Managed detection and response illustrates this shift: eSentire now protects data for 2.5 million patients, underscoring demand in regulated fields.
The North America cybersecurity market size for managed services is expanding fastest among healthcare and mid-market manufacturing firms. Service-based consumption models help firms consolidate sprawling toolsets and secure board approval by treating cybersecurity as an operating expense. Vendors, in turn, bundle AI, threat intelligence, and human expertise, capturing sticky multiyear contracts and boosting recurring revenue visibility.
On-premise deployments still made up 56.2% of the North America cybersecurity market size in 2024, but cloud security spending is advancing at 17.2% CAGR as hybrid work exposes perimeter-centric gaps. Federal zero-trust mandates, coupled with executive orders on cloud-first strategies, accelerate cloud-native adoption in defense and civil agencies. For private-sector adopters, the pivot lowers capital expenditure, integrates policy orchestration, and enables continuous compliance.
Large enterprises operate hybrid models for data-sovereignty reasons, while SMEs leapfrog straight to fully managed cloud-security service edges. Oracle's framework for zero-trust cloud controls demonstrates how identity governance, micro-segmentation, and encryption converge to tighten attack surfaces. Vendors that automate policy creation and misconfiguration remediation find traction as multicloud complexity scales.
North America Cyber Security Market is Segmented by Offering (Solutions and Services), Deployment Mode (Cloud and On-Premise), Organization Size (Small and Medium Enterprises and Large Enterprises), End-User (BFSI, Healthcare, IT and Telecom, and More), and Country. The Market Forecasts are Provided in Terms of Value (USD).