
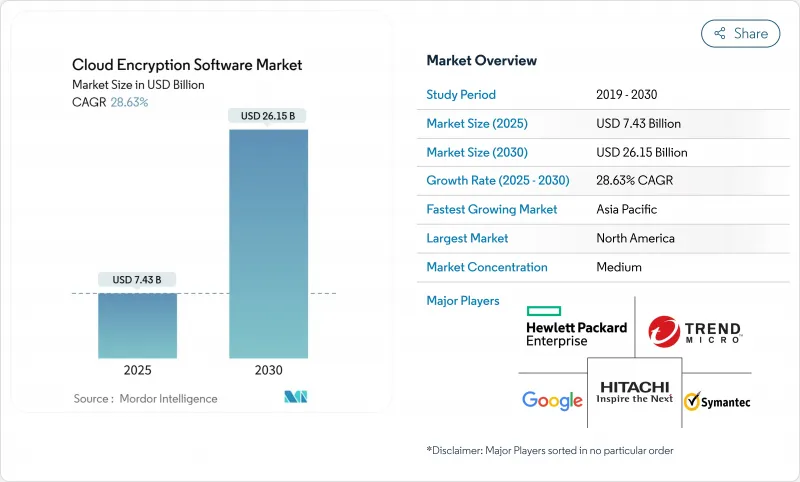
클라우드 암호화 소프트웨어 시장 규모는 2025년에 74억 3,000만 달러, 2030년에는 261억 5,000만 달러에 이르고, CAGR 28.6%를 나타낼 전망입니다.

이 급성장은 세 가지 강력한 힘, 즉 용서하지 않는 사이버 공격, 규제 압력 증가, 멀티 클라우드 컴퓨팅으로의 업무 변화가 융합한 것입니다. 미국립표준기술연구소(NIST)가 2024년 8월 최종 결정한 포스트 양자암호의 표준은 '지금 암호를 해독해 버린다(harvest-now-decrypt-later)'위험이 이미 나타나고 있음을 이사회가 인식했기 때문에 기업의 마이그레이션 로드맵을 가속시켰습니다. 동시에 금융 서비스 기업의 98%가 퍼블릭 클라우드에서 워크로드를 운용하고 있으며, 이종 플랫폼간에 통일된 열쇠 관리가 시급합니다. 북미는 FedRAMP와 국방부가 양자안전 알고리즘을 의무화하고 있으며, 아시아태평양은 주권 클라우드 정책에 따라 CAGR이 가장 빠른 지역이 되고 있습니다. 암호화 에코시스템은 성능에 최적화된 대칭 도구, 획기적인 완전 호모모픽 암호화, 사용 중인 데이터를 밀봉하는 하드웨어 지원 기밀 컴퓨팅 기술로도 형성됩니다.
세계 법규에 따라 보안 기준치가 증가하고 있습니다. PCI DSS 4.0(2025년 3월 발효)은 모든 카드 소지자 환경에서 연 1회 암호화 검토 및 다중 요소 인증을 의무화합니다. 유럽의 디지털 운영 탄력성 법과 NIS 2 지침은 은행 업무와 중요 인프라에 대해 2030년까지 내량자 암호화를 의무화하고 있습니다. 미국에서는 양자 컴퓨팅 사이버 보안 준비법이 연방 정부 기관에 NIST가 승인한 포스트 양자 알고리즘으로의 이행을 의무화하고 있으며, 민간 섹터가 이를 흉내내는 병형이 되고 있습니다. FedRAMP는 이미 모든 연방 정부 클라우드 서비스에 대해 FIPS 140-2의 검증된 모듈을 의무화하고 있으며, 컴플라이언스는 사실상 시장 진입권이 되고 있습니다. 2002년에 제정된 FERPA의 틀에서는 학생 데이터가 클라우드에 저장될 것으로 예상되지 않았기 때문에 대학에서도 관리를 강화하고 있으며, 법적인 최저 기준을 넘는 암호화 대책이 요구되고 있습니다.
클라우드 워크로드는 2024년에 기록된 사이버 인시던트의 31%를 흡수했으며 금융 서비스의 랜섬웨어 비용은 평균 537만 달러에 달했습니다. 고도의 영구적 위협을 갖춘 기업은 향후 양자암호 해독에 내기하여 암호화된 데이터를 수집합니다. 따라서 실시간암호화 감시와 고전적인 키 교환과 포스트 양자 키 교환의 하이브리드가 인기를 끌고 있습니다. 퍼블릭 클라우드 침해의 44%는 구성 실수로 인한 것이므로 관리자의 기술에 의존하지 않고 모든 개체를 암호화하는 자동 정책 엔진이 필요합니다. 공격자는 엔드포인트가 아닌 제어 플레인의 ID를 대상으로 하고 있으며 경계 제어가 실패하더라도 효과를 유지할 수 있는 데이터 중심 보호가 필요합니다.
데이터를 암호화하면 계산주기와 i/O 대기 시간이 늘어납니다. 고전적인 Atrest 암호화를 사용하면 대용량 데이터베이스의 SQL 쿼리가 수백 밀리초 느려집니다. 완전 호모모픽 암호화는 프라이버시 측면에서 획기적이지만 하드웨어 가속을 사용하지 않는 한 처리 시간이 1,000배로 늘어납니다. Computers, Materials and Continua 잡지에 게재된 최근의 벤치마크 연구에 따르면, GPU 지원 프레임워크는 이 오버헤드를 약 12% 삭감합니다. 엣지 컴퓨팅 시나리오에서는 암호화 지연이 기존 네트워크 지연을 악화시키므로 설계자는 실시간 응답성과 기밀성을 저울에 넣어야 하며 이 패널티를 가장 강하게 느낄 수 있습니다. 또한 포스트 양자 알고리즘은 키 크기가 커지므로 계산 부하가 높아지고 저전력 장치에서 성능 버짓 문제가 발생합니다.
2024년 클라우드 암호화 소프트웨어 시장 점유율은 35.6%로 신메트릭 방식이 압도적이며 그 속도와 CPU 오버헤드의 낮음을 지지하고 있습니다. 완전 호모모픽 암호화는 여명기에도 불구하고 가장 빠르게 성장하는 기술이며 기밀 컴퓨팅 이용 사례가 확대됨에 따라 CAGR 29.0%를 나타낼 것으로 예측됩니다. 2024년 8월에 출시된 FIPS 203, FIPS 204, FIPS 205는 포스트 양자 키 캡슐화, 디지털 서명 및 상태 비저장 해시 기반 서명 기준선을 설정했으며 공급업체는 이러한 알고리즘을 제품 로드맵에 통합하도록 촉구했습니다.
기업은 고전적인 타원 곡선법과 포스트 양자 격자를 융합시킨 하이브리드 암호를 도입하여 알고리즘의 실패를 헤지하고 있습니다. 레거시 용도이 스키마를 재설계하지 않고 보호된 데이터를 저장할 수 있기 때문에 형식 유지 암호화도 확대되고 있습니다. NIST가 2025년 3월에 HQC를 5번째 알고리즘으로 선정하고 더 많은 다양성을 요구했기 때문에 암호화 애자일 툴은 이사회 수준의 우선사항이 되었습니다. 결과적으로 대칭 워크로드의 클라우드 암호화 소프트웨어 시장 규모는 꾸준히 상승하고 양자 안전 옵션이 새로운 도입의 큰 부분을 차지할 것으로 예측됩니다.
2024년 클라우드 암호화 소프트웨어 시장에서 데이터 어트레스트는 36.8%의 점유율을 차지하며 용도 스택의 최고였습니다. 그러나 주목받는 것은 사용 중인 데이터 암호화이며, TEE가 일반 텍스트 처리라는 오랜 장벽을 없애면서 CAGR29.7%로 급증하고 있습니다. 따라서 민감한 워크로드를 위한 클라우드 암호화 소프트웨어 시장 규모는 다른 모든 부문보다 빠르게 확장됩니다.
전송 계층 보호는 클라우드 간 링크에 필수적인 것은 아니지만 성능 튜닝은 포스트 양자 핸드셰이크 알고리즘으로 이동합니다. SaaS 협업 도구는 클라이언트 측 암호화를 광범위하게 배포하며 조직은 암호화 키 관리를 유지합니다. 검색 가능한 대칭 암호화는 고가의 쿼리에 대한 대기 시간 오버헤드를 허용하는 빅 데이터 환경에서 등장했습니다. 이러한 변화가 결합되어 데이터 라이프 사이클 전반에 걸쳐 상태에 관계없이 영구적인 보호라는 비전이 추진되고 있습니다.
북미는 2024년에 클라우드 암호화 소프트웨어 시장의 38.9%를 차지하며, FedRAMP의 의무화, 국방부 지령, 기업의 포스트 양자 제어로의 적극적인 이행에 지지되었습니다. 멀티클라우드의 보급률이 높고, 벤더는 매니지드 키 서비스와 암호화 애자일 오케스트레이션을 통해 수익을 확보하고 있습니다. 헬스케어와 금융의 선도적인 고객도 기밀 컴퓨팅 프레임워크를 대규모로 테스트하여 혁신 사이클을 가속화하고 있습니다.
아시아태평양은 2030년까지 연평균 복합 성장률(CAGR)이 29.5%로 가장 급성장하고 있는 지역입니다. 호주, 일본, 한국, 인도의 주권 클라우드 설계도에서는 암호화 키가 국내에 머무르는 것이 요구되고 있으며, 외래 키 관리 게이트웨이와 필요에 따라 각국의 알고리즘을 지원하는 하드웨어 보안 모듈의 판매에 박차가 걸려 있습니다. 아시아 개발 은행은 클라우드 정책 개선으로 2024년부터 2028년까지 이 지역의 GDP를 최대 0.7% 밀어올릴 수 있을 것으로 예측하고 있으며, 암호화는 그 극히 중요한 실현 요인으로 꼽혔습니다. 중국과 동남아시아의 하이퍼스케일러는 양자 안전 네트워크 암호화를 제공하기 위해 칩 제조업체와 국내에서 제휴를 맺고 있으며, 구미의 라이벌과 보조를 맞추고 있습니다.
유럽에서는 GDPR(EU 개인정보보호규정)의 시행과 디지털 오퍼레이션 탄력성법(Digital Operational Resilience Act)이 추진력이 되어 꾸준한 확대가 계속되고 있습니다. 금융기관은 양자내성 알고리즘으로의 전환을 보여주는 탄력계획의 제출을 의무화되고 있으며, 이 움직임은 유럽을 국경을 넘은 키 에스크로 상호운용성의 실험장으로 변모시키고 있습니다. 프라이버시를 보호하는 분석, 특히 의료 및 이동성 분야에서 완전 동형 암호화에 대한 수요가 증가하고 있습니다. 남미와 중동 및 아프리카의 소규모 시장은 특히 5G 배포로 가볍고 저지연 암호화가 필요한 에지 클라우드 아키텍처를 도입하는 등 그린 필드 기회를 제공합니다.
The cloud encryption software market size stands at USD 7.43 billion in 2025 and is on course to reach USD 26.15 billion by 2030, registering a 28.6% CAGR.
The surge blends three powerful forces: unrelenting cyber-attacks, mounting regulatory pressure, and the operational shift toward multi-cloud computing. Post-quantum cryptography standards finalized by the National Institute of Standards and Technology (NIST) in August 2024 accelerated enterprise migration road maps as boards realized that harvest-now-decrypt-later risks have already materialized. At the same time, 98% of financial-services firms now operate workloads in public cloud, creating an urgent need for unified key management across heterogeneous platforms. North America leads adoption, propelled by FedRAMP and Department of Defense mandates for quantum-safe algorithms, while sovereign-cloud policies push Asia-Pacific to the fastest regional CAGR. The encryption ecosystem is also shaped by performance-optimized symmetric tools, breakthrough fully homomorphic encryption, and hardware-assisted confidential-computing technologies that seal data during use.
Worldwide statutes are raising the security baseline. PCI DSS 4.0, effective March 2025, forces annual cryptographic reviews and multi-factor authentication across all card-holder environments. Europe's Digital Operational Resilience Act and NIS 2 directive require quantum-resistant encryption by 2030 for banking and critical infrastructure. In the United States, the Quantum Computing Cybersecurity Preparedness Act compels federal agencies to pivot to NIST-approved post-quantum algorithms, setting a template the private sector is following. FedRAMP has already mandated FIPS 140-2 validated modules for all federal cloud services, turning compliance into a de facto market entry ticket. Even universities are hardening controls because the 2002 FERPA framework never anticipated cloud-stored student data, prompting encryption measures that exceed legal minima.
Cloud workloads absorbed 31% of recorded cyber incidents in 2024, with ransomware costs in financial services averaging USD 5.37 million. Advanced persistent-threat actors now harvest encrypted troves, betting on future quantum decryption. Real-time encryption monitoring and hybrid classical-plus-post-quantum key exchange are therefore gaining traction. Misconfigurations cause 44% of public-cloud breaches, so automated policy engines that wrap encryption around every object-independent of administrator skill-are becoming mandatory. Attackers increasingly target control-plane identities rather than endpoints, reinforcing the need for data-centric protection that stays effective even when perimeter controls fail.
Encrypting data adds compute cycles and I/O waits. Classical encryption-at-rest slows SQL queries by several hundred milliseconds in high-volume databases. Fully homomorphic encryption, while revolutionary for privacy, can inflate processing time by 1 000X unless hardware acceleration is employed. GPU-assisted frameworks cut that overhead by roughly 12% according to recent benchmark studies published in Computers, Materials and Continua. Edge-computing scenarios feel the penalty most because encryption delay compounds existing network latency, forcing architects to weigh real-time responsiveness against confidentiality. Post-quantum algorithms also raise computational tax because of larger key sizes, challenging performance budgeting in low-power devices.
Other drivers and restraints analyzed in the detailed report include:
For complete list of drivers and restraints, kindly check the Table Of Contents.
Symmetric methods dominate the cloud encryption software market with 35.6% share in 2024, favored for their speed and low CPU overhead. Fully homomorphic encryption, despite its infancy, is the fastest-rising technique, forecast to grow at 29.0% CAGR as confidential-computing use cases blossom. The August 2024 release of FIPS 203, FIPS 204, and FIPS 205 set the baseline for post-quantum key encapsulation, digital signatures, and stateless hash-based signatures, prompting vendors to embed these algorithms into product road maps.
Enterprises are deploying hybrid cryptography that blends classical elliptic-curve methods with post-quantum lattices, hedging against algorithmic failure. Format-preserving encryption is also expanding because it lets legacy applications store protected data without schema redesign. With NIST's March 2025 selection of HQC as a fifth algorithm for additional diversity, crypto-agile tooling has become a board-level priority. As a result, the cloud encryption software market size for symmetric workloads is projected to climb steadily, while quantum-safe options capture a larger slice of new deployments.
Data-at-rest still tops the application stack with 36.8% share of the cloud encryption software market in 2024, reflecting mature backup and storage practices. Yet it is data-in-use encryption that makes headlines, surging at a 29.7% CAGR as TEEs remove the longstanding barrier of processing on plaintext. The cloud encryption software market size for confidential-computing workloads will therefore expand faster than any other segment.
Transport-layer protection remains indispensable for inter-cloud links, but performance tuning has shifted toward post-quantum handshake algorithms. SaaS collaboration tools are seeing wider client-side encryption rollouts so organizations retain control over cryptographic keys. Searchable symmetric encryption now appears in big-data environments, where latency overhead can be tolerated for high-value queries. Together these shifts advance the vision of persistent, state-agnostic protection across the entire data life cycle.
The Cloud Encryption Software Market Report is Segmented by Encryption Type (Symmetric, Asymmetric / PKI, and More), Application (Data-At-Rest, Data-In-Transit, and More), Organization Size (Large Enterprises and Small and Medium Enterprises (SMEs)), Industry Vertical (BFSI, Healthcare and Life Sciences, Education, Retail and E-Commerce, and More), and Geography. The Market Forecasts are Provided in Terms of Value (USD).
North America held 38.9% of the cloud encryption software market in 2024, underpinned by FedRAMP mandates, Department of Defense directives and aggressive enterprise migration to post-quantum controls. Multi-cloud penetration is high, and vendors secure revenue through managed key services and crypto-agile orchestration. Large healthcare and finance clients also test confidential-computing frameworks at scale, accelerating innovation cycles.
Asia-Pacific is the fastest-growing region with a 29.5% CAGR through 2030. Sovereign-cloud blueprints in Australia, Japan, South Korea and India demand that encryption keys remain on domestic soil, spurring sales of external key-management gateways and hardware security modules that support national algorithms where required. The Asian Development Bank estimates improved cloud policy could lift regional GDP by up to 0.7% during 2024-2028, and encryption is cited as a pivotal enabler. Chinese and Southeast Asian hyperscalers are forming in-country alliances with chipmakers to deliver quantum-safe network encryption, keeping pace with Western rivals.
Europe maintains steady expansion driven by GDPR enforcement and the Digital Operational Resilience Act. Financial institutions must file resilience plans outlining migration to quantum-resistant algorithms, a move that is turning Europe into a laboratory for cross-border key-escrow interoperability. Privacy-preserving analytics-especially in health and mobility-stimulate demand for fully homomorphic encryption. Smaller markets in South America and the Middle East and Africa trail but present greenfield opportunities, particularly where 5G rollouts introduce edge-cloud architectures that require lightweight, low-latency encryption.